How Whalebone’s threat intelligence makes a difference
Discover how Whalebone detects and prevents cyber threats with AI-driven analytics and real-time security for your organization. ...

Whalebone offers an IT security solution designed to protect businesses from online threats such as malware, ransomware and phishing attacks.
Protects against cyber threats with protective DNS Immunity
Blocks malicious domains and gets rid of unwanted traffic
Protects all devices without the need to install software
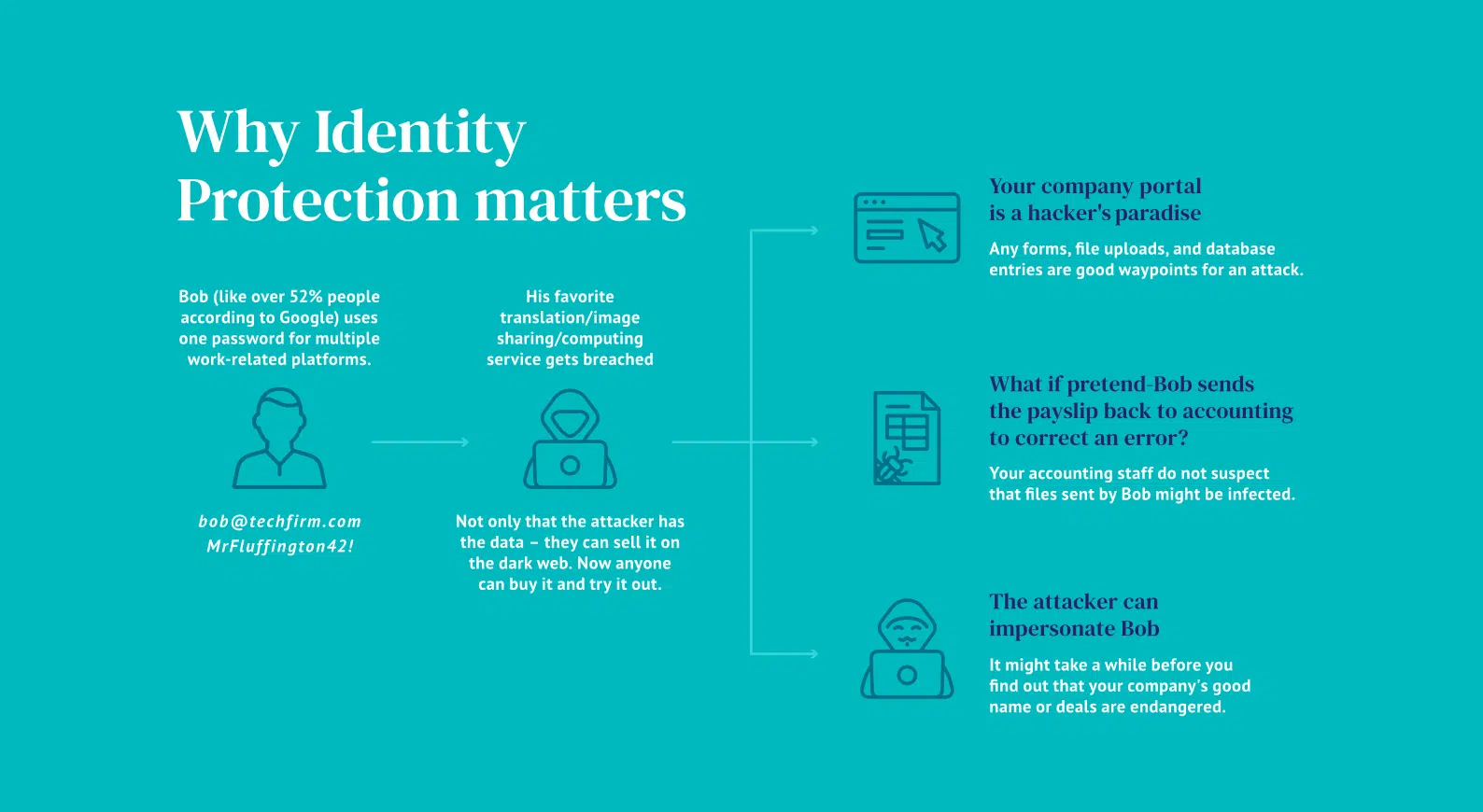
Includes Identity Protection and off-net protection
Instant security for all users and devices.
No installation, all devices are protected
No maintenance or additional staff required
Whalebone Immunity provides businesses and institutions with an essential layer of protection – a complete control over the DNS traffic regardless of size or complexity of their network. More than 90% of malware uses DNS resolution at some point during its life cycle, so in this layer you can stop attacking strategies which elude firewall, end-point protection, and other traditional protection methods.
The majority of organisations still do not have direct control over their DNS resolution, nor do they monitor and filter their DNS traffic. This makes them vulnerable to:
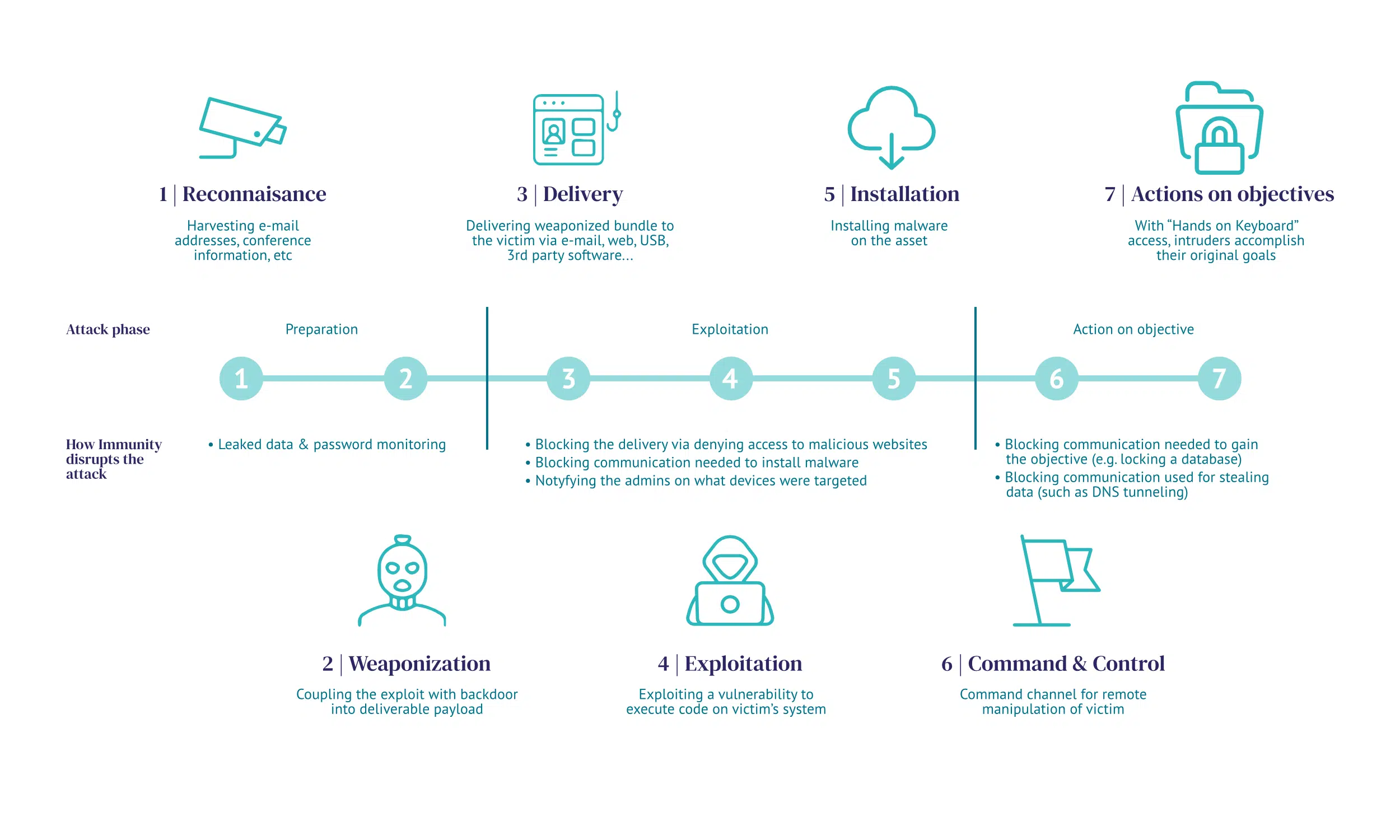
When it comes to DNS resolution, firewalls just look at the individual DNS queries to identify threats, and are therefore reliant on databases of known codes used for above-mentioned tactics. Whalebone analyses patterns using AI which allows it to distinguish behaviour connected to DNS tunneling, DGAs, and wide range of malware, stopping even the threats which are not a part of any database yet (0-day threats).
Moreover, additional features of Whalebone Immunity ensure coverage of other blind spots in the standard security stack:
To sum up, without DNS protection, there are multiple blind spots in the security perimeter. Moreover, thanks to not needing installation in the end devices, Immunity does not require almost any maintenance and thus saves your IT team time and resources. And last but not leads, it adds a security layer to gain maximum confidence that the network is as protected as possible in case there is any malfunction or insufficient threat intelligence in the other security layers.
Find a detailed list of key elements below:
Whalebone Immunity – a fast and stable recursive DNS resolver with sophisticated security modules – is scalable and fits network of any size, whether smaller companies or enterprises with multiple sites and international branches. Usually the cloud version can be up and running in 1 hour, after which the whole network including computers, mobile phones, cameras, servers, printers, and any other IoT devices are immediately protected.
For the easiest and fastest deployment there is a cloud version of Whalebone Immunity, while on-premise deployment offers deeper insight into the DNS traffic up to the level of a single device, which allows to pinpoint exactly which device or user was targeted. Usually, the on-premise deployment takes up to 4 hours to deploy, after which the whole network including any device connected to the internet is immediately protected.
The free trial version lasts 30 days, during which the full functionality, including the Identity protection feature, is available. Around 50% of customers find out that there is malicious traffic not blocked by their other security stack during the trial version, and approximately 50% of customers identify leaked sensitive data using the Identity Protection feature.
Find out how Whalebone Immunity saves your time and effort here.
Apart from the standard threat intelligence sources (public and paid databases and threat intelligence feeds), Whalebone utilizes unique measures to ensure that any threat is identified and filtered on DNS level as soon as possible:
The goal of Whalebone is to protect 1 billion people worldwide. It is a global leader in telecommunication consumer security, one of 25 fastest growing companies in Central Europe, and a leader of the DNS4EU association which was hand-picked by the European Commission to develop and operate an official DNS resolver for the European Union.
Discover how Whalebone detects and prevents cyber threats with AI-driven analytics and real-time security for your organization. ...
Discover our trusted European technology brands. Secure, connected, and innovative solutions designed for the future. Learn more now!...
Discover which DNS vendors excel in security and speed. Contact us for detailed insights!...