
26 Feb Enhancing Cybersecurity Through Asset and Vulnerability Detection
Introduction
In an era where cyber threats are increasing exponentially, organizations face the immense challenge of securing ever-expanding attack surfaces. With the proliferation of Internet of Things (IoT) devices, cloud environments, and remote work infrastructures, traditional cybersecurity solutions often fall short in providing comprehensive visibility and control.
Many companies have no idea which devices are connected to their network. The network is the backbone of the business, connecting users and devices to each other and to the internet. It is highly beneficial as network connectivity enhances automation and work efficiency. However, this also increases the risk of being vulnerable to cyberattacks.
That is why tools that enable asset visibility and vulnerability detection are so essential to a company’s cybersecurity strategy. Everything starts with the question, “What is in our network?” By answering this question, a company can begin planning how to properly protect these devices.
Within Kappa Data’s portfolio, two groundbreaking solutions are revolutionizing the way organizations approach asset visibility, threat detection, and network security.
What does this solution do exactly?
Both Armis and runZero share a common mission: to provide organizations with complete insight into their network environments and protect them against vulnerabilities and threats. The core objective is to ensure that every device, whether managed or unmanaged, is accounted for and secured against modern cyber risks. Their shared vision focuses on:
- Visibility across the entire attack surface: Identifying and understanding all connected assets, including IoT devices, shadow IT components, and other unmanaged endpoints.
- Risk mitigation: Proactively detecting vulnerabilities and suspicious behavior to prevent breaches.
- Operational continuity: Strengthening security without disrupting business operations. OT environments can be highly sensitive, so scanning and detection must run in the background without interrupting OT business continuity.
While their approaches and industry focuses may differ, both solutions aim to empower organizations to build resilient cybersecurity frameworks that adapt to evolving threats.
Armis: Enterprise-Level Anomaly Detection for Assets and Traffic
Armis is an enterprise solution tailored for securing unmanaged and IoT devices, with a particularly strong presence in critical sectors such as healthcare and hospitals. The platform continuously analyzes network traffic, identifying anomalies and threats in real-time to protect connected assets and ensure operational safety.

Where Armis truly excels:
- Protection of medical and IoT devices: Secures medical devices such as infusion pumps, MRI machines, and industrial IoT systems.
- Traffic anomaly detection: Continuously monitors network traffic and analyzes the behavior of sources and destinations to detect malicious and suspicious activities. This includes signature-based threats such as Log4j and SQL injection, but also behavioral pattern analysis for brute force attacks, port scans, malicious host connections, and abnormal asset behavior.
- Global threat intelligence integration: Correlates data with threat intelligence to proactively identify and mitigate risks.
RunZero
Formerly known as Rumble, runZero specializes in discovering and cataloging every device connected to a network. It provides organizations with detailed, real-time insights into all assets, including IoT devices, unmanaged endpoints, and shadow IT components. Using non-intrusive scanning methods, runZero ensures complete visibility without disrupting network operations.
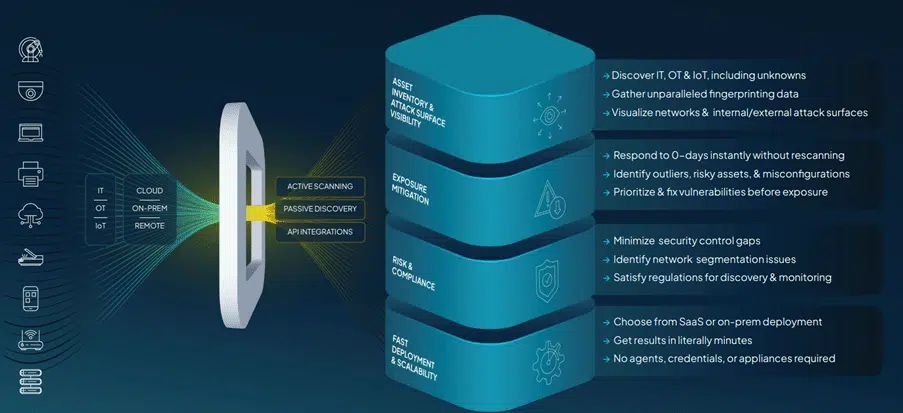
The discovery of these assets must be done in multiple ways. RunZero is designed to recognize, discover, and gain insights into assets through different techniques:
- Agentless Discovery: runZero operates entirely without agents. Unlike other solutions that require agents to be deployed on assets, runZero scans the network without manual intervention.
- Detailed asset inventory: runZero discovers devices through active scanning, passive discovery, and API integrations, enabling it to gather detailed information about assets, including operating systems, services, and vulnerabilities.
- Seamless deployment: runZero is quick to set up and provides an intuitive interface for teams of all sizes.
Why Are These Solutions Necessary?
The cybersecurity landscape is evolving rapidly. As organizations adopt more connected devices and transition to hybrid environments, gaps in traditional security frameworks become evident. This is why solutions like Armis and runZero are so critical:
- Growing IoT adoption: Gartner predicts that by 2030, there will be over 25 billion IoT devices, many of which lack built-in security.
- Proliferation of shadow IT: Employees, contractors, and third parties often connect unauthorized devices to networks, creating security blind spots. RunZero reports that 25% of the assets it discovers were previously unknown to business customers. Even air-gapped devices are sometimes found exposed to the internet.
- Advanced threats: Cybercriminals increasingly target unmanaged and IoT devices as easy entry points. Armis and runZero address these challenges by providing visibility, control, and protection for every connected device.
Integration with Other Vendors and Products
The true power of these platforms lies in their ability to integrate with leading cybersecurity and network management solutions. Examples include:
- Network Access Control (NAC): If an unauthorized device is detected, NAC can enforce rules to assign it to a designated network segment.
- IP Address Management (IPAM): Many businesses use IPAM solutions to track assigned IP addresses, assets, and networks. These solutions help simplify IP management.
- XDR/MDR: Endpoint protection solutions offer real-time visibility for managed devices. Integrating both solutions bridges the gap between managed and unmanaged devices, ensuring a unified threat response.
- SIEM and SOAR platforms: Feeds detailed asset and threat intelligence into Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms for streamlined incident response.
Conclusion
Asset discovery and vulnerability management platforms represent the next generation of cybersecurity solutions, closing critical visibility and protection gaps in today’s complex IT environments. Every cybersecurity journey starts with understanding what exists within the business network before it can be protected in the best possible way.
By integrating with other leading vendors, these platforms enable organizations to build robust, scalable, and proactive security ecosystems. As cyber threats continue to evolve, using innovative solutions like Armis and runZero is no longer optional.
Next Steps if you are interested in these solutions, sign up for the free trial of runZero via https://runzero.com/try/ and be sure to contact [email protected] for more information or to set up a Proof of Value with Armis.



No Comments