
04 May NIS 2: What can we do right now?
“What the GDPR is for ensuring privacy, the NIS2 is for cybersecurity at the EU level.”
NIS 2 is a European Network and Information Systems Security Directive (NIS 2) with a set of regulations to ensure the security and resilience of network and information systems across the European Union (EU). The NIS 2 directive will seek to improve cybersecurity in the European Union in various ways. In the Netherlands, the NIS is also known as the NIS directive.
Now that EU countries have adopted the NIS 2 directive at the end of 2022, two years remain for the various member states to transpose it into national legislation. So, we can expect new legislation in the fall of 2024. The obligations for organizations covered by it should then realistically take effect in early 2025. But of course, you don’t have to wait until 2025 to invest in cyber security for your organization!
Difference of NIS from NIS2
The first version of NIS (NIS1) has two categories of sectors, critical (essential) or critical infrastructure and digital service providers. NIS 2 is much broader and some of these sectors now named differently. It also expands the number of sectors and clarifies which providers now fall under them. Because NIS 2 now introduces uniform rules, it means that member states no longer have to designate essential providers individually.
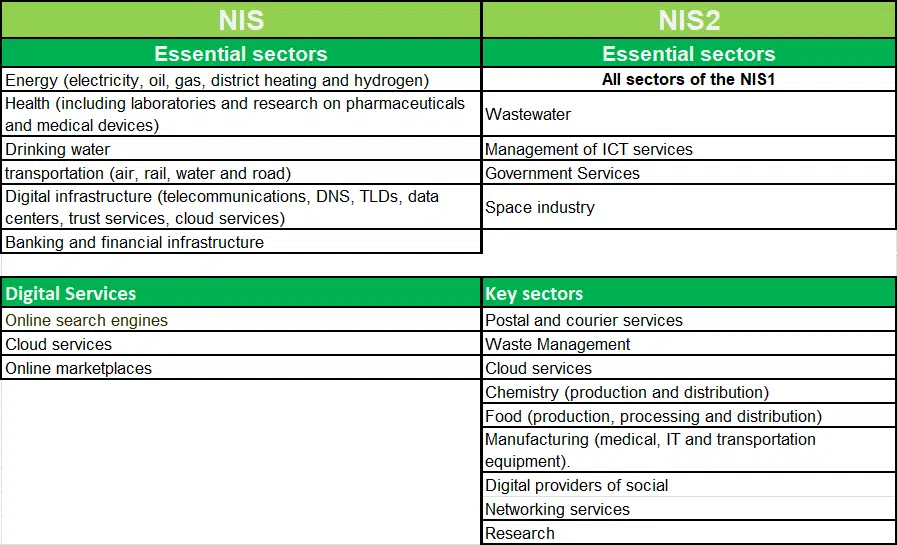
ls your organization is situated in the important sectors in the table NIS2, you will soon have to comply with the NIS2 directive. The biggest difference in label “essential” or “important” is in monitoring and compliance.
Obligations
A distinction is made between two components: duty of care and duty of notification.
- Duty of care: a list of measures they must comply with as a minimum. These include crisis management in the event of a major cyber incident, performing risk assessments and using encryption. (ISO 27001 standard)
- Duty to report: report when they face a cyber incident. That reporting requirement now only applies to data breaches (GDPR), but so it will now become mandatory to report things like a ransomware attack or serious abuse.
For whom?
An entity that operates in any of the above sectors and had (in its last two financial years) more than 50 employees or an annual turnover of more than €10 million (i.e. large or medium-sized enterprises) will have to comply with the Directive’s requirements.
In addition to the “essential sectors,” NIS2 now defines a second category, the “important sectors.” The difference between “essential” and “important” lies in the degree of supervision. Essential sectors are subject to proactive supervision, while important sectors are subject to reactive supervision.
TIP: Check whether your organization falls under the NIS2 regulations directly or indirectly as a supplier. The Center for Cybersecurity Belgium (CCB) said some 2,400 Belgian companies would be covered by the new NIS2 legislation.
Security requirements
NIS2 goes a step further than NIS 1 by establishing security requirements for key and critical sectors. This includes the certification of products, services and processes under specific EU cybersecurity certification schemes.
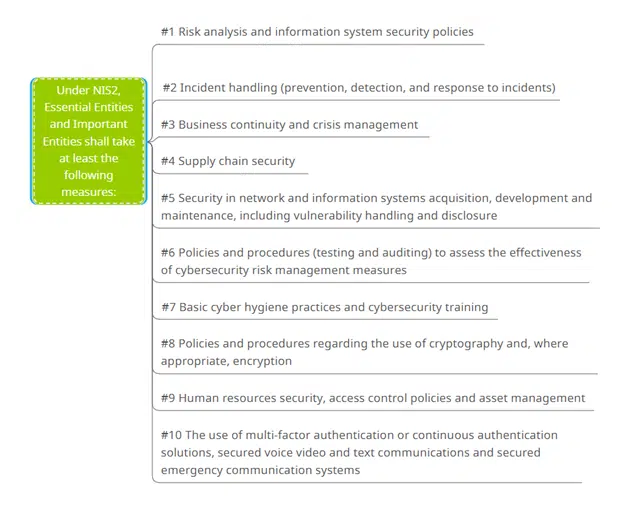
The NIS-2 Directive will simply state (see Article 18) that entities must have: incident management plans, activity continuity plans and crisis management plans, policies and procedures to assess the effectiveness of these measures, as well as policies on the use of cryptography, personnel security, the use of appropriate authentication systems and supply chain management.
Depending on the level of maturity of your organization’s security, the topics below are key areas for improvement:
Fines
Think GDPR-like fines! Essential organizations that are large enough and do not meet the requirements set by the NIS2 directives could be fined up to 10 million euros or 2 percent of total global annual sales The intention is to have stricter oversight and more consistent enforcement and fines across member states.
NIS 2 turns the thumbs up on all fronts compared to NIS1: broader scope, security requirement, notification requirement, and stricter enforcement.
What measures to take for NIS 2 compliance?
Implement risk-based cybersecurity management!
To protect networks and systems and their physical and their physical environment from incidents, those measures must support a risk-based approach. Supplemented by the necessary e (external) security controls.
The NIS 2 guideline provides an example of an ideal state of security, but one that is easily achievable with the right guidance and investment.
The “appropriate” and “proportionate” measures to be taken to secure network and information systems can be divided into organizational (1) and technical measures (2).
1. Compliance & Goverance
NIS 2 includes many elements already defined in best security and compliance frameworks (e.g., IEC62443, NIST, ISO27001). So investing in existing cybersecurity frameworks can enable organizations to address risks covered by NIS 2:
- Have risk analysis performed,
- Business continuity and crisis management plan
- Outlined policies and documented procedures.
- Security awareness training for staff and awareness management
- Handling and reporting of incidents.
2. Technical measures to secure infrastructure and applications
Infrastructure & application security:
- Next-generation firewall
- Blocks traffic, services, ports and protocols except those expressly authorized and defined as appropriate and necessary for the organization.
- Vendors: Barracuda, Sophos, Stormshield
- Antivirus on all endpoints and servers with at least XDR/EDR capabilities:
- Antivirus that uses AI and machine learning to do exploit prevention, behavioral protection, anti-ransomware and that automatically identifies suspicious activity, can prioritize threat indicators and quickly search for potential threats on your endpoints and servers.
- Vendors: Sophos
- Managed Detection & Response (MDR) service:
- Identity and access control solution (IAM):
- User-based technology to have role-based user-level control over network resources and other organizational assets.
- Vendors: One Identity
- ZTNA (Zero Trust Network Access).
- Highly granular access controls by validating user identity and device health and compliance before granting access to systems or application.
- Vendors: Barracuda, Sophos, Cato Networks, One Identity
- MDM (mobile device management).
- Protection for mobile devices – even for users working with personal devices. Flexible compliance rules monitor device health and flag deviations from desired settings.
- Vendors: Sophos
- Device & File encryption
- Protect devices and data with full encryption. Check encryption status of devices and demonstrate compliance.
- Vendors: Sophos
- Asset Management
- Proactive approach through inventory of all assets and vulnerability handling
- Vendors: Armis
- Centralization monitoring and alerting
- Monitor and correlate signals from across the network, identify and investigate suspicious activity on the network infrastructure to optimize cyber defense.
- Vendors: Solarwinds



No Comments